When enterprises implement low-code security automation solutions, they have the opportunity to mature as a security team by expanding actionability beyond the security operations center (SOC). This means that they automate use cases beyond the basic security orchestration automation and response (SOAR) use cases, like phishing. Once security teams move high-volume work off their plate, they are able to automate security processes dealing with areas like identity, risk management, network, privacy, DevOps, and much more.
One Swimlane customer, who I’ll refer to as Bank Mega, has improved its risk posture by automating response to credential compromises to prevent fraud. This use case came out of a situation where they detected an attempt of wire transfer fraud. By fully automating investigation and response to credential compromises, Bank Mega significantly reduced their dwell time, improved their risk posture, and saved analyst time. Between automating credential compromises and phishing alone, customers like Bank Mega typically save an entire full-time employee (FTE).
The Wire Transfer Fraud Event
Bank Mega’s customer reported that they received an invoice from Bank Mega’s email system which asked the customer to redirect an invoice payment. Thankfully, the customer realized this email was “phishy”, so they did not pay the invoice. Instead, the customer reached out to Bank Mega with an updated and expanded vendor security assessment. It was sent using credentials found to have been exposed on a dumpsite on the “Dark Web”.
Low-Code Security Automation for Credential Monitoring
Bank Mega knew that they needed a manageable solution to ensure that they, and their customers, aren’t exposed to potential wire transfer fraud events like this again. To strengthen their security posture they subscribed to a credential compromise monitoring service, through Recorded Future, which they integrated with Swimlane, their low-code security automation tool.
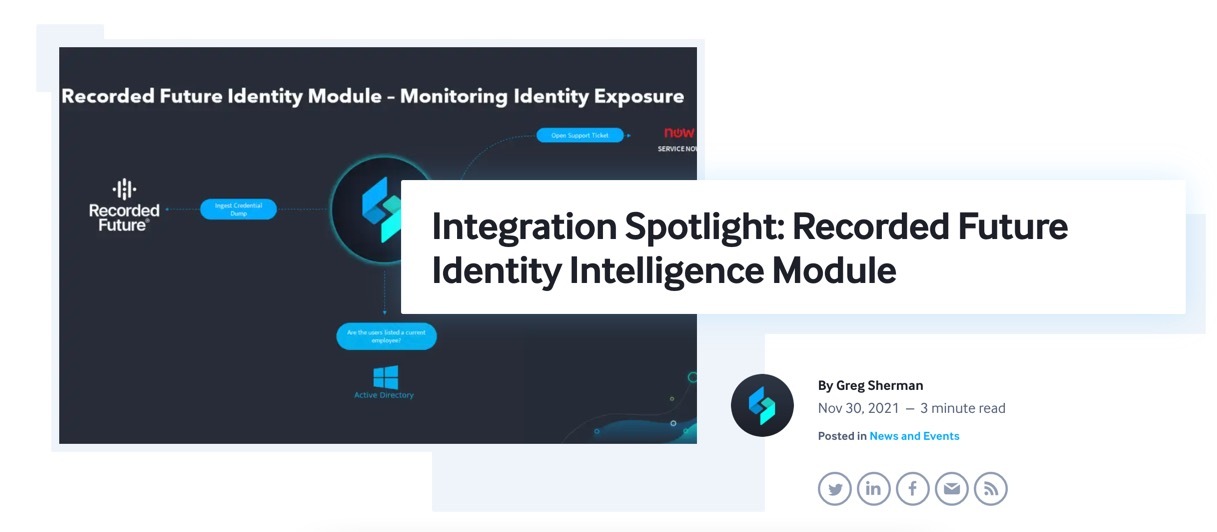
Swimlane and Recorded Future Demo
This Swimlane and Recorded Future demo from our Co-founder and Chief Strategy Officer, Cody Cornell, and Director of Solution Architecture, Bryon Page, shows how this use case works in 5 simple steps.
1. Domain Retrieved
Bank Mega leveraged Recorded Future’s API plugin and Swimlane’s low-code security automation platform to scan specific identities and domains that needed to be monitored. Now, scans for attempted credential dumps automatically occur every 24 hours. Swimlane stack ranks the results as low, medium, high or critical based on the identity found.
2. Identity Investigated
One way that Swimlane enriches Recorded Future’s threat intelligence of compromised credentials is by querying Bank Mega’s HR Management System (HRMS), to determine if the compromised credentials belong to an active user or former employee. If Swimlane identifies that the compromise involves an active user, it queries Bank Mega’s Identity Access Management (IAM) provider to determine what systems or applications the user has access to. It knows this based on if the user is a system administrator, HR, legal, an individual contributor, etc. These findings are an example of how Swimlane scores credential compromise criticality.
3. Password Hash Validated
At the same time that this is happening, Swimlane runs other queries to investigate if the compromised credentials are valid. It does this by taking the hashes that are dumped from various sources, like the Dark Web or collection lists, to understand if it is a valid hash.
4. Slack Notification Sent
In cases when the compromise is a current employee and the credentials are confirmed to be valid, Bank Mega does not want to wait for the analyst to resolve this issue. So, they use Swimlane to send the user an automated message via Slack to let them know that their credentials will be reset in 30 minutes. Automated messages could also be sent through systems like email or SMS.
5. Password Reset
Then, as the Slack notification indicated, Swimlane resets the password in 30 minutes. This action concludes the workflow and effectively resolves the credential compromise.
Results that reduce 3rd party risk
The demo video shows the value of monitoring credentials for Bank Mega’s own employees. Increasingly, we are seeing customers apply this use case for monitoring credentials belonging to 3rd party service providers or partners. These partners typically have access to corporate environments like vendor and partner portals. When companies add partners to their monitoring list, they can greatly reduce 3rd party risk associated with having interconnected systems.
Reach out to us here to learn more about how Swimlane and Recorded Future work together to automate your threat intelligence use cases.
Integration Spotlight: Recorded Future Identity Intelligence Module
Monitoring, Evaluating, and Responding to Credential Dumps


