As cyberattacks become more sophisticated and costly, the importance grows for maintaining security controls to improve your organization’s risk posture.
Cybersecurity is a growing concern for today’s organizations, with more and more sensitive information being stored and transmitted online. To combat the growing threat of cyber attacks, organizations have developed various frameworks to help ensure the security of their systems and data.
What is a cybersecurity framework?
A cybersecurity framework is a set of guidelines and best practices that organizations can use to manage and reduce their security risk. The frameworks provide a comprehensive approach to cybersecurity that covers all aspects of an organization’s operations, from the boardroom to the data center. They are designed to help organizations better understand and manage their cybersecurity posture, make informed decisions about their security investments and defend against potential threats and vulnerabilities.
Here are some of the top cybersecurity frameworks you should know:
NIST Cybersecurity Framework
Developed by the National Institute of Standards and Technology (NIST), this framework provides a comprehensive approach to managing cybersecurity risk for organizations of all sizes and types. The framework is based on five key functions:
- Identify
- Protect
- Detect
- Respond
- Recover
The NIST Cybersecurity Framework provides a roadmap for improving cybersecurity and can be used as a benchmark for evaluating an organization’s cybersecurity posture. The framework is widely used by organizations of all sizes, including government agencies and critical infrastructure operators.
MITRE ATT@CK Framework
MITRE ATT@CK is a comprehensive, open-source framework for threat modeling and analysis. Developed by the MITRE Corporation, the framework provides a standardized way to describe and analyze cyber threats.
The framework covers a wide range of threat actors, tactics and techniques. It also includes information on the tools, infrastructure and motivations behind each attack. This information can be used to better understand the threat landscape and improve your organization’s ability to detect and respond to attacks. It’s also regularly updated with new information on emerging threats and best practices, making it a valuable resource for security professionals.
MITRE ATT@CK uses a matrix to map out the various stages of an attack. These include initial access, execution, persistence, privilege escalation and more. This matrix provides a clear and concise way to understand the tactics and techniques used by different threat actors and can help organizations prioritize their security efforts.
Learn how to use security automation to automate ATT@CK testing.
CIS Critical Security Controls
The Center for Internet Security (CIS) Critical Security Controls are a set of 18 best practices for cybersecurity, designed to help organizations prioritize their efforts and resources. The controls are organized into three categories:
- Basic
- Foundational
- Organizational
A key benefit of CIS Controls is the focus on actionable, results-driven measures that can be implemented quickly and effectively. The controls are updated on a regular basis to keep pace with the evolving threat landscape. Organizations are encouraged to use these as a starting point for their cybersecurity efforts.
NERC-CIP Standards
The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC-CIP) is a set of mandatory, industry-wide cybersecurity standards for the protection of critical infrastructure in the electric sector.
NERC-CIP covers a wide range of topics, including access control, incident response, configuration management, and physical security. The standards are organized into seven different security controls, each of which addresses a different aspect of cybersecurity. Organizations are required to implement these controls to ensure the protection of critical assets, such as control centers, substations, and transmission lines.
Watch how automation can streamline NERC-CIP incident response.
Organizations are required to conduct risk assessments to identify potential cybersecurity threats and to implement measures to mitigate these risks. The standards also require organizations to regularly assess their security posture to ensure protection against emerging threats.
CISA TSS Framework
The Cybersecurity and Infrastructure Security Agency (CISA) Transportation Systems Sector (TSS) Cybersecurity Framework is a set of guidelines and best practices for securing transportation systems in the United States. It was developed by the CISA, which is part of the Department of Homeland Security, in partnership with the transportation sector.
The TSS Cybersecurity Framework is designed to help transportation systems organizations understand and manage their cybersecurity risk. The framework covers a wide range of topics, including access control, incident response, risk management, and supply chain security. The framework is intended to be used in conjunction with other cybersecurity frameworks and standards, such as NIST or ISO 27001.
Risk management is a core focus of the TSS Cybersecurity Framework. The framework provides guidance on how to assess and manage cybersecurity risk, including how to prioritize and implement security controls. The framework also includes guidelines for incident response and information sharing, which are critical components of an effective cybersecurity program.
NCSC Cyber Assessment Framework
The National Cyber Security Centre (NCSC) Cyber Assessment Framework (CAF) is a set of guidelines and best practices for assessing and improving an organization’s cybersecurity posture. The NCSC is part of the UK’s GCHQ (Government Communications Headquarters). It’s responsible for providing cybersecurity advice and support to the UK government and critical national infrastructure.
The CAF grants organizations a structured approach to assessing their cybersecurity and identifying areas for improvement. It covers a wide range of topics, including access control, incident response, risk management, and supply chain security. The framework is intended to be used in conjunction with other cybersecurity frameworks and standards, such as NIST or ISO 27001.
The framework provides guidelines for regular assessments and updates, allowing organizations to stay up-to-date with the latest cybersecurity best practices and threats. The CAF also includes guidelines for incident response and information sharing, which are critical components of an effective cybersecurity program. The use of the CAF is not a legal requirement, but its adoption is encouraged for organizations in the UK.
ISO 27001 Standard
This is an international standard for information security management, developed by the International Organization for Standardization (ISO). It provides a systematic approach to managing sensitive information, including the implementation of security controls, risk assessment, and incident management.
ISO 27001 outlines a systematic and risk-based approach to information security management, covering all aspects of information security, including people, processes, and technology. The standard covers a wide range of topics, including access control, incident management, cryptography, network security, and physical security.
The standard requires organizations to identify and assess their information security risks, prioritize their security controls, and implement measures to mitigate those risks. The standard also requires organizations to regularly review and update their information security management systems to ensure that they remain effective and up-to-date.
SOC 2 Compliance
The Service Organization Control (SOC) 2 is a set of standards for information security, privacy, and data protection. It focuses on ensuring that service providers have appropriate security controls in place to protect customer data. It is maintained by the American Institute of Certified Public Accountants (AICPA).
SOC 2 is designed for service organizations, such as cloud service providers and SaaS providers, that store or process customer data in the cloud. The SOC 2 standards focus on five trust service principles: security, availability, processing integrity, confidentiality, and privacy.
To comply with SOC 2, organizations must undergo a formal audit and certification process. The audit assesses the organization’s information security and privacy controls, including their policies, procedures, and technology systems. The auditor issues a report that details the results of the audit and provides recommendations for improvement.
By familiarizing yourself with these top cybersecurity frameworks, you can better understand the steps your organization can take to protect against cyber threats. It’s important to stay up-to-date on the latest best practices and trends in the field of cybersecurity.
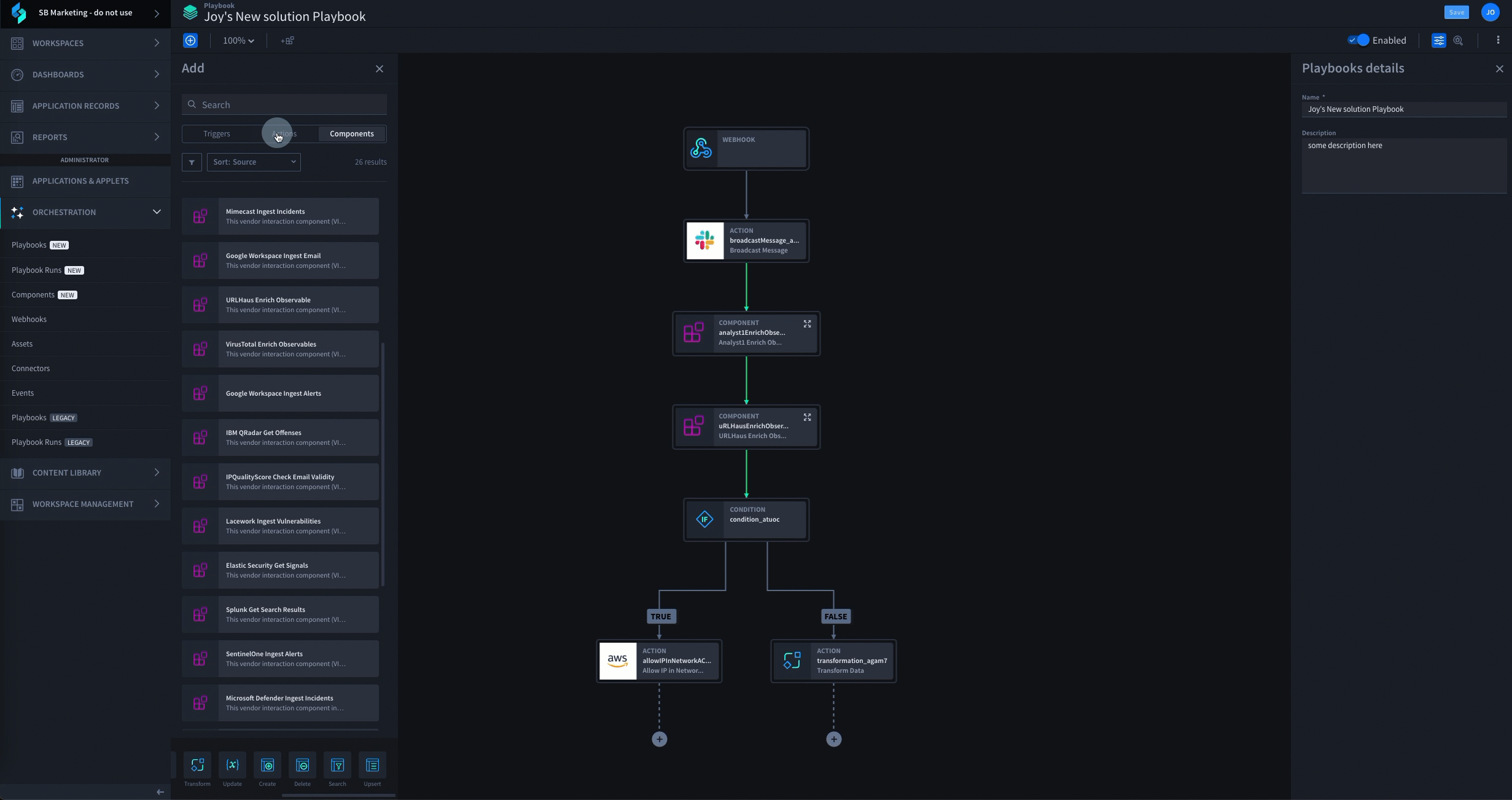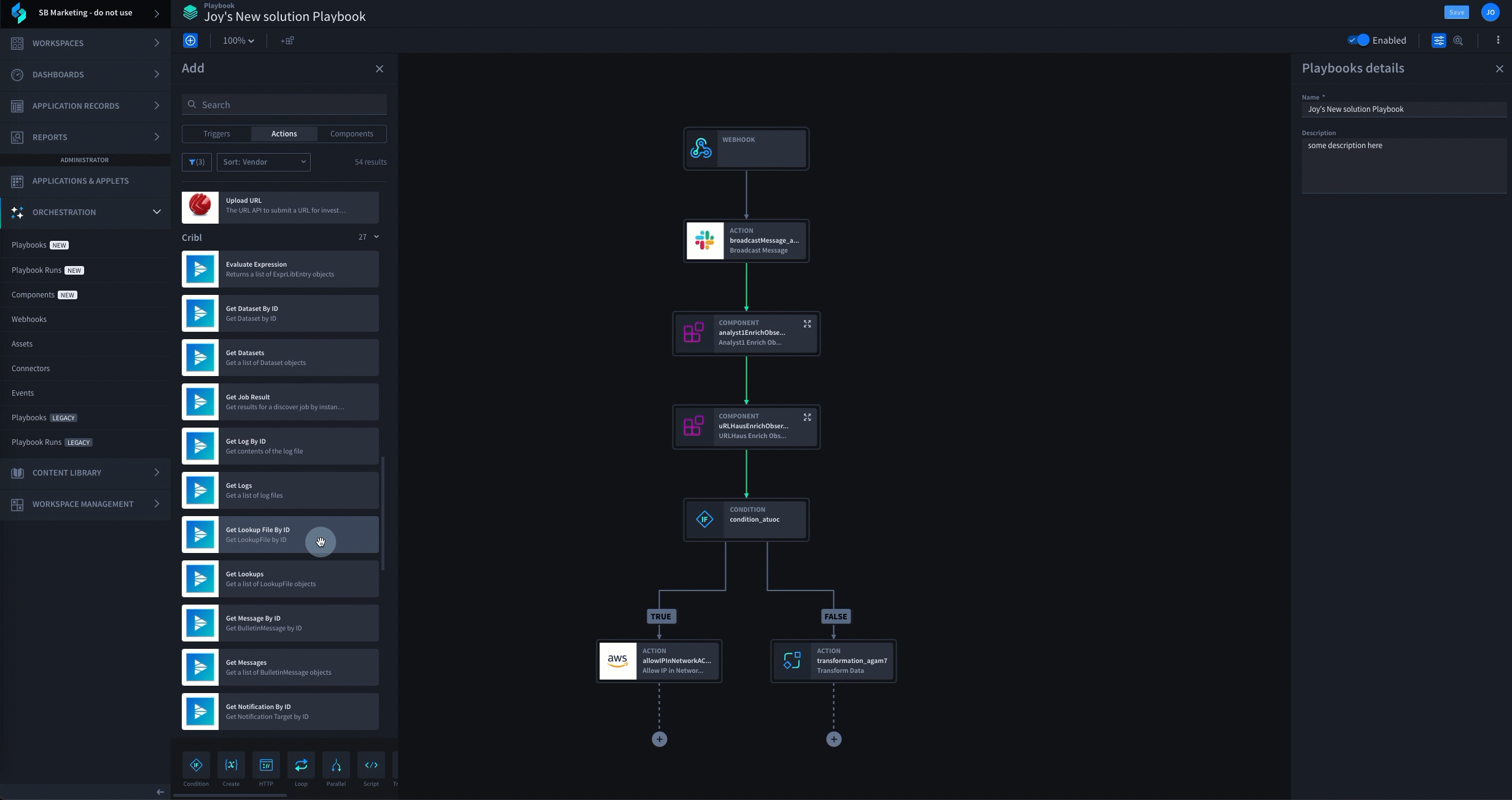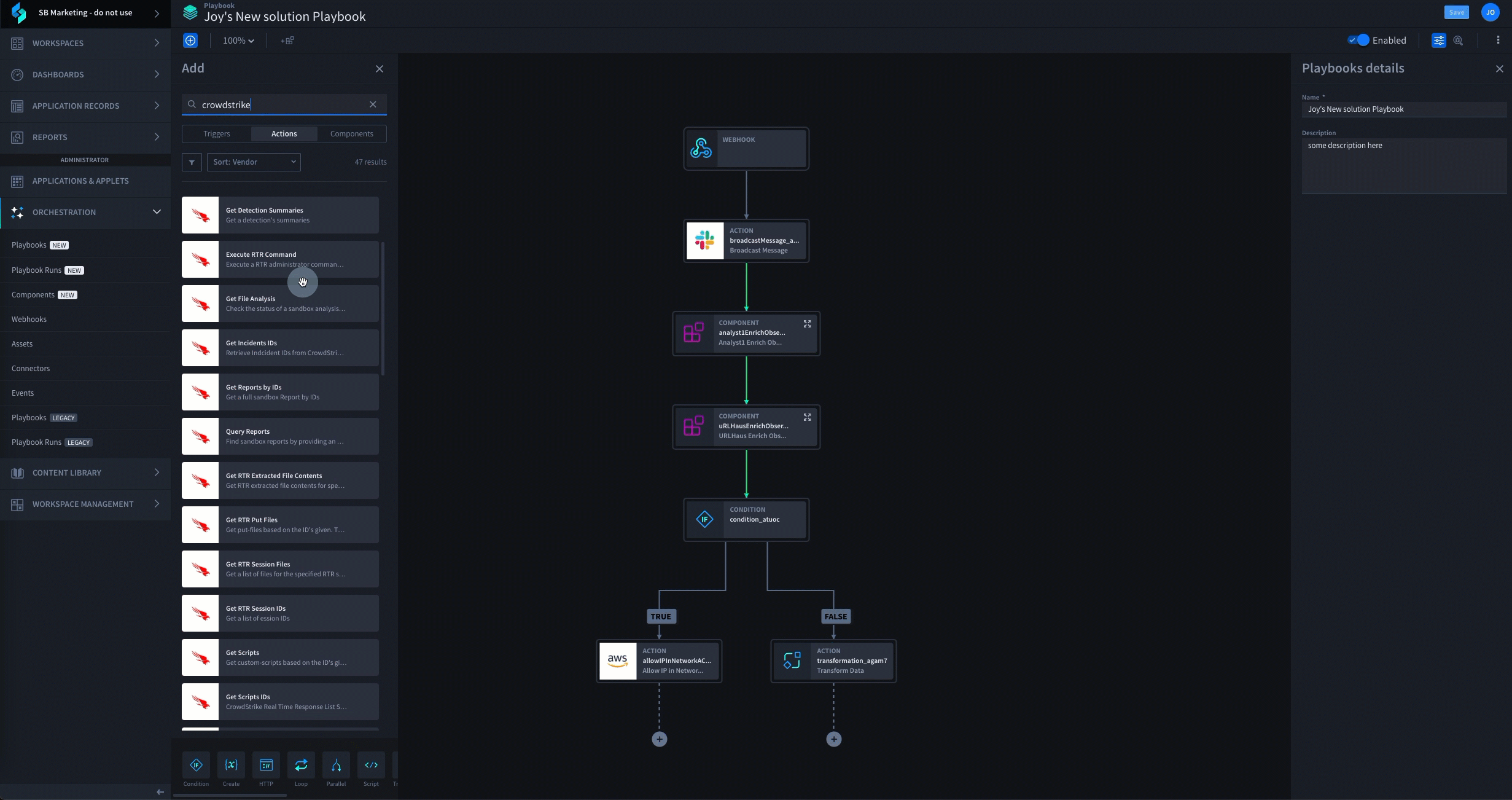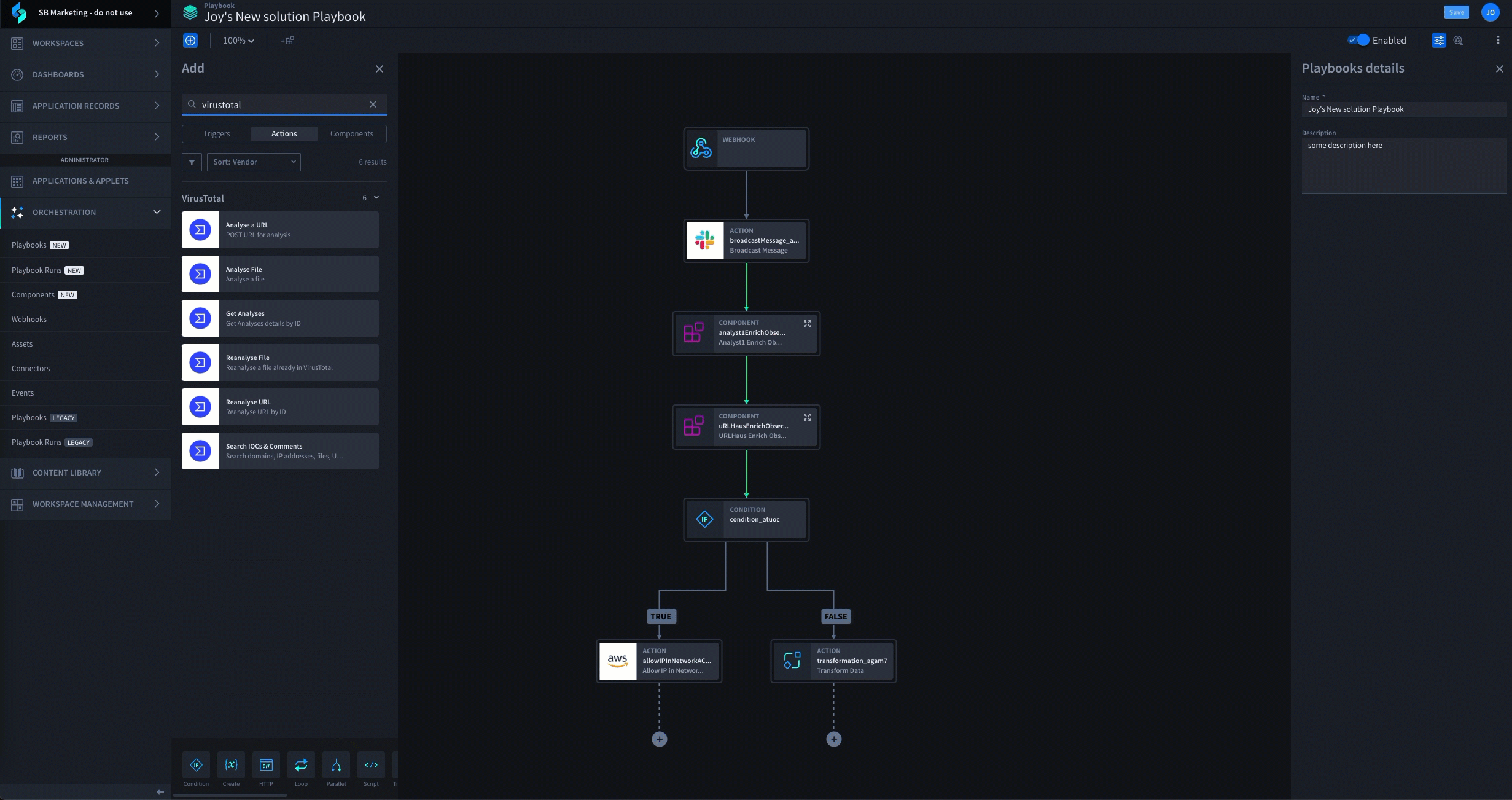
See Swimlane Turbine in Action
Schedule a Swimlane Turbine live demonstration with our experts! Learn how our AI-enabled security automation platform can help you solve the most challenging problems across your entire security organization.