With the increasing sophistication of cyber threats, it’s crucial to balance the speed and efficiency that security automation brings against the need for human oversight and intuition. With this being said, there are instances where an organization should automate security and instances where they shouldn’t, or shouldn’t, just yet. Let’s get right into it.
The Benefits of Automated Cybersecurity
Automated cybersecurity tools offer many benefits, significantly enhancing an organization’s defense mechanisms against various types of cyber attacks.
So, Why Automate Cybersecurity?
- Efficiency and Speed: Automated security can process and analyze vast volumes of data at a pace no human SecOps team can match, instantly identifying and responding to threats, which ultimately reduces the time between detection, response and important security metrics.
- Empowers Human Teams: Automated security handles routine tasks, allowing human security experts to focus on more strategic initiatives and complex problem-solving, leveraging their skills where they are most needed.
- Cost Reduction: By automating routine and repetitive tasks, organizations can reduce the need for a large cybersecurity staff, leading to significant cost savings. Additionally, preventing breaches can save potential costs related to data loss, legal fees, and reputation damage.
- 24/7 Monitoring: Cyber threats can occur at any time. Automated systems ensure continuous monitoring and protection, providing security around the clock without the need for constant human supervision.
- Consistency and Reliability: SOC analysts can make errors, overlook details, or become fatigued, but automated systems consistently apply the same standards and rules, reducing the risk of human error.
- Scalability: As organizations grow, their cybersecurity needs become more complex. Automated security can easily scale up to handle increased data and more sophisticated network environments without a proportional increase in resources or costs.
- Proactive Defense: Automated systems can predict and prevent attacks before they happen, using predictive analytics and machine learning to identify potential threats based on historical data and current trends.
- Enhanced Compliance: Many industries are subject to strict regulatory requirements for data protection. Automated security helps ensure compliance with these regulations by systematically enforcing policies and keeping detailed logs of security events.
- Improved Threat Detection and Incident Response (TDIR): In the event of a security breach, automated tools can immediately contain the threat and mitigate damage, significantly reducing the impact on the organization.
- Comprehensive Coverage: Automated cybersecurity can monitor all aspects of an organization’s digital footprint, including endpoints, networks, and cloud services, providing comprehensive protection against a wide range of threats.
When NOT to Automate Security
We here at Swimlane are firm believers in automating cybersecurity, and clearly, there are many benefits; however, there are places where automation should take the backseat. Here are a few examples where SOC automation shouldn’t take preference:
1. Undocumented Processes
When a SOC process has not been documented before, and there is uncertainty about all the steps involved, automating it can introduce significant risks and inefficiencies. Security automation relies on predictability and a clear understanding of the process flow to be effective. Without a comprehensive understanding and documentation of the steps involved, automating the process can lead to critical oversights.
Moreover, undocumented processes often have nuances and exceptions that are understood and managed by human analysts, and they can be difficult to encode into an automated system without a detailed analysis. Attempting to automate such a process prematurely can also freeze its current state, making it harder to optimize and improve the process over time.
2. Alerts That Need to be Modified at Source
Automating alerts that require tuning or modification at your Security Information and Event Management (SIEM) or alert source can be counterproductive. Premature automation can lead to a flood of false positives, overwhelming security teams and diverting attention away from genuine threats. It’s crucial to first refine these alerts, ensuring their accuracy and relevance. This fine-tuning process allows for the identification of the precise conditions under which alerts should be triggered, minimizing noise and enhancing the overall efficiency of the SecOps team.
3. When ROI is Not Going to be Worth it
Sometimes, the return on investment (ROI) does not justify the initial and ongoing costs of security automation. When the projected benefits, such as reduced breach risk or efficiency gains, don’t outweigh the expenses of implementing and maintaining sophisticated automation tools, it’s crucial to reconsider. This is because automation, while extremely valuable, requires substantial upfront investment in technology, training, and integration. Moreover, it needs ongoing expenses related to updates, management, and, potentially, scaling. Completing an ROI calculator can ensure your organization considers the investment in full and doesn’t automate prematurely.
4. When There is a Risk of Business Disruption
If the automation is not properly aligned with the organization’s operational workflows, it could inadvertently block legitimate activities or fail to accommodate exceptions, leading to downtime or impairing critical functions. This is especially true in complex environments where security needs are tightly interwoven with business operations, so caution should be exercised when considering automation in areas where there is a risk of disruption, as the consequences could outweigh the intended security benefits.
When to Automate Security
Now, if you’re looking to build a modern SOC, having the right automation in place, at the right time, is crucial.
Organizations Should Automate Security…
After Documenting Processes
Automating security after thorough process documentation and testing is a foundational step that ensures each task and workflow is clearly understood, defined and mapped out so it can effectively identify potential vulnerabilities or inefficiencies. Once this groundwork is laid, automation can be effectively implemented to achieve faster threat detection and incident response (TDIR), consistent application of security policies, reducing future edge cases, and freeing up human resources.
To Manage SecOps Efficacy
One of the main reasons for automating security is that it dramatically improves SecOps efficacy by enabling the processing and analysis of vast volumes of data at a speed unattainable by human teams. This rapid, round-the-clock identification and response to threats significantly reduce the time between detection and resolution, which is crucial in mitigating potential damage.
By automating routine and repetitive tasks, such as scheduling KPI reporting and security metrics, organizations can also allocate their skilled security personnel to more strategic, high-level tasks that require human intuition and expertise. This not only optimizes the use of valuable human resources but also allows for a more proactive and strategic approach to cybersecurity.
For Breach Prevention
As mentioned, cyber threats continue to evolve at an alarming pace, far beyond the capacity for manual SecOps monitoring and response. Automation leverages advanced technologies like artificial intelligence and machine learning to continuously scan and protect digital assets, ensuring that potential breaches are detected and mitigated in real time. This proactive approach significantly reduces the likelihood of successful attacks and also maintains a strong security posture, safeguarding sensitive data and maintaining trust with their clients and stakeholders.
To Mitigate Alert Fatigue
Alert fatigue occurs when security personnel are overwhelmed by a constant influx of alerts, many of which may be false positives, leading to a situation where critical alerts might be overlooked or dismissed. By implementing automation, organizations can filter out the noise of false positives and streamline the alert management process. This ensures that only genuine threats are escalated to human SOC analysts, allowing them to focus on resolving true security incidents efficiently.
To Standardize Processes
Automating security is essential for standardizing processes across an organization. This standardization is paramount because it ensures that all steps are followed in order, reducing the likelihood of mistakes and ensuring that all parts of the organization adhere to the same high standards of security. By automating routine, repetitive security tasks and developing procedures for performing incident handling, organizations can establish a uniform approach to cybersecurity. This uniformity not only enhances overall security posture but also improves accuracy, efficiency and reliability as it leaves less room for vulnerabilities that can arise from inconsistent security practices.
To Give Extra Information About Alerts
Another critical aspect of strengthening security through automation involves providing additional information for alerts, such as data enrichment for vulnerabilities and indicator of compromise (IoC) enrichment. Automating these processes not only streamlines the identification and assessment of potential threats but also enables security teams to respond more swiftly, enhancing overall security resilience.
To Ensure Compliance
Automated systems can consistently enforce evolving security policies and regulations, monitor for compliance in real time, and maintain detailed logs of security events without the lapses or inconsistencies that can happen with manual oversight. By systematically applying security rules and procedures, such as 2FA and correct user permissions, automation helps organizations remain compliant and reduces the risk of breaches and the subsequent legal and financial repercussions of non-compliance. This consistent and adaptable approach not only protects against threats but also safeguards an organization’s reputation by maintaining the trust of customers and its stakeholders.
To Connect Siloed Security Tools
Organizations often deploy a variety of tools designed to protect different aspects of their network and data. However, these tools can become isolated, operating independently of one another, which creates gaps in defense mechanisms. Through security automation, these disparate systems can be integrated, allowing for seamless communication and data sharing between them. With integration, detection and response capabilities become optimized by streamlining workflows and providing a comprehensive view of security threats.
How to Automate Security Best Practices?
To effectively automate security best practices, leveraging advanced security automation tools is vital. The steps to automate a manual process are:
- Begin by conducting a thorough assessment of your security needs and identifying areas where automation can provide the most benefit, such as TDIR and compliance management.
- Choose a SOC vendor with the solutions, use cases and innovative capabilities required to manage the complex security needs of your organization.
- Select security automation tools that offer robust integration capabilities, ensuring they can seamlessly work with your existing security infrastructure.
- Implement tools that utilize artificial intelligence and machine learning to adapt to new threats dynamically and perform routine security tasks, such as patch management, vulnerability scans, and log monitoring, to provide proactive protection.
- Ensure continuous improvement by frequently reviewing and updating the automation rules and parameters to keep up with the evolving cybersecurity landscape.
Automate Security with Swimlane Turbine
Swimlane Turbine is the triple threat of automation. With the right security automation tools in place, organizations can significantly enhance their ability to implement SOC best practices, ensure compliance and prevent breaches, guaranteeing a resilient and responsive security posture.
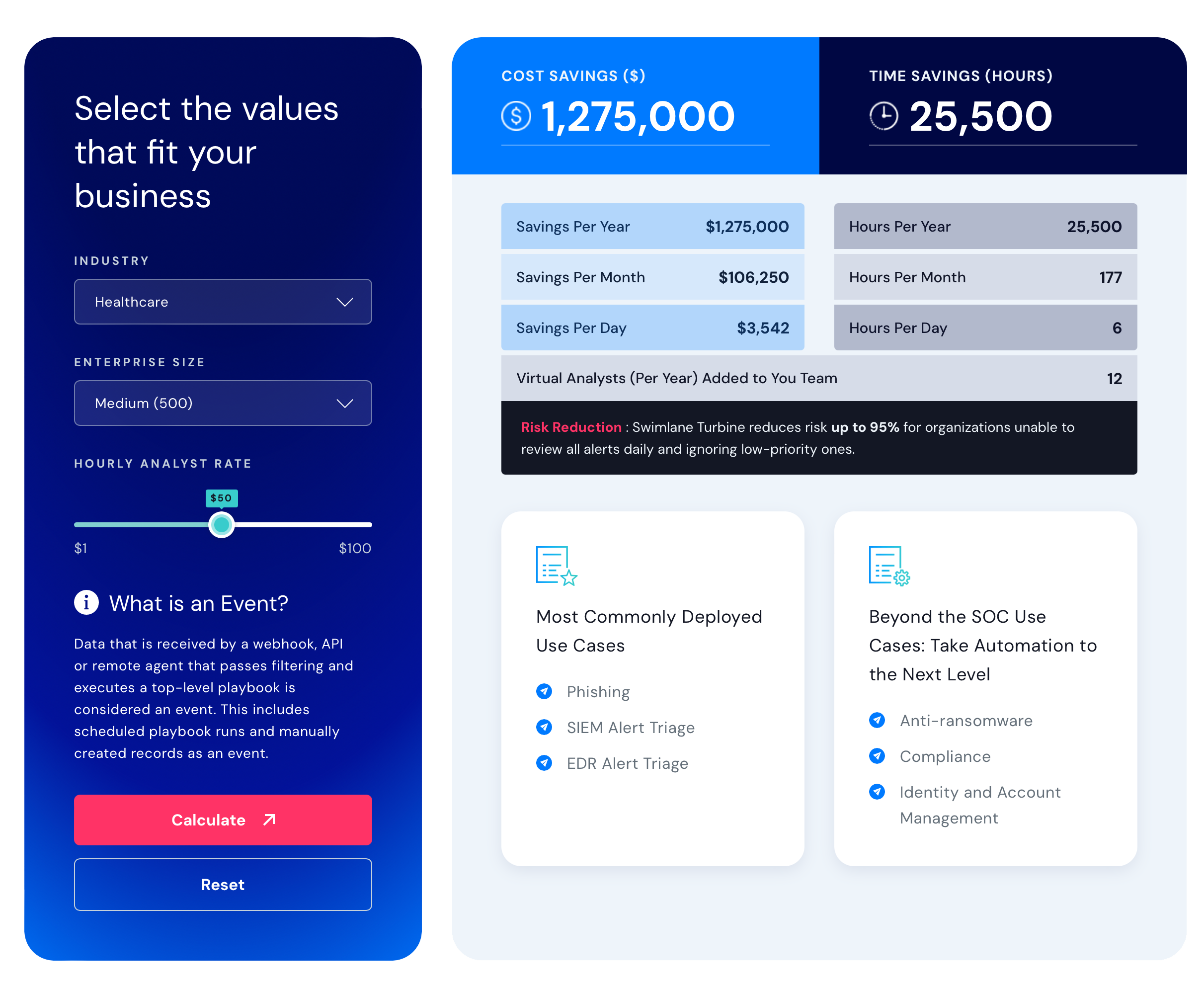
Swimlane ROI calculator
Estimate the savings you can achieve with Swimlane Turbine.

