It should be the unwritten rule of cybersecurity: Don’t make an asymptote of yourself or your team members.
As you may recall from high school math, an asymptote is a graphical representation of a function that trends endlessly either toward zero or infinity. In the case of threat response, the potential cost of a delay can resemble the latter — draining the corporate wallet at an ever-accelerating pace. For those of you who miss Algebra II, Figure 1 offers an example of what we’re talking about.
How can cybersecurity get asymptotic? (Just to bring in a little SAT prep and AP English while we’re at it…) The problem stems from the increasing level of business impact from an unchecked threat. As the model in the table shows, as each day goes by with a delay in threat response, the costs start to add up.
| Day | Security Team | Senior IT Leadership | Executive Leadership | Legal | Public Relations | Outside Security Consultants | Settlements and Fines | Reputation Damage | Cumulative Total Cost |
|---|---|---|---|---|---|---|---|---|---|
| 1 | $50 | $50 | |||||||
| 2 | $500 | $550 | |||||||
| 3 | $1,000 | $2,500 | $4,050 | ||||||
| 4 | $5,000 | $5,000 | $5,000 | $5,000 | $24,050 | ||||
| 5 | $5,000 | $5,000 | $5,000 | $5,000 | $5,000 | $49,050 | |||
| 6 | $5,000 | $5,000 | $5,000 | $5,000 | $5,000 | $10,000 | $84,050 | ||
| 7 | $5,000 | $5,000 | $5,000 | $5,000 | $5,000 | $10,000 | $119,050 | ||
| 8 | $5,000 | $5,000 | $5,000 | $25,000 | $20,000 | $10,000 | $189,050 | ||
| 9 | $5,000 | $5,000 | $5,000 | $25,000 | $20,000 | $10,000 | $259,050 | ||
| 10+ | $5,000 | $5,000 | $5,000 | $20,000 | $100,000 | $10,000 | $1,000,000 | $1,000,000 | $2,484,050 |
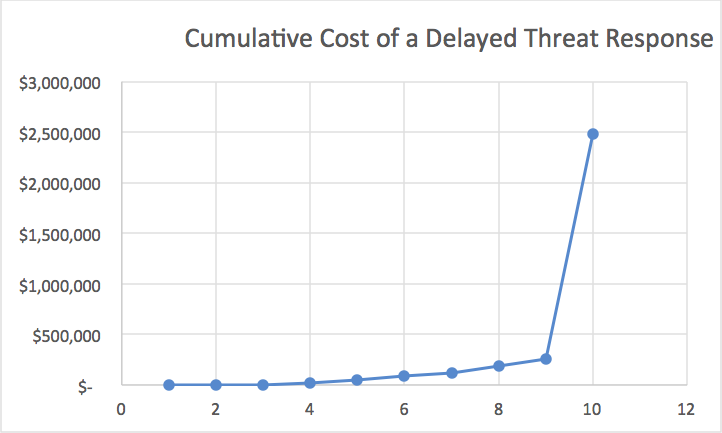
How threat handling costs grow quickly
This model shown in the table is highly simplified example. What matters are the pattern and trend, which are realistic. Threats generally don’t get cheaper the longer they are ignored or go unnoticed. A malicious intrusion, if caught immediately, might have a negligible cost to fix. If the intrusion turns into a breach, the security team will have to start devoting many person-hours to figure out what happened, what’s been affected and how remedy the situation.
If the problem starts to affect the business itself, such as by slowing down or corrupting critical systems, senior business leadership will get involved. Everyone’s time is valuable. When the CEO is focusing on a security breach, that’s time he or she is not spending on making the company grow. More people, including expensive outsiders like attorneys, PR firms and security consultants, may get involved if the threat metastasizes into a true disaster. What started as a simple threat might end up triggering multi-million dollar fines and settlements as well as reputation damage. Figure 2 depicts the cumulative cost of a delayed threat response, taken from the table, in graphic form. As you can see, it’s asymptotic.
Speeding up threat response
New advances in security operations management and automation make it possible to speed up the process of detecting and responding to a threat. Automated incident response and security orchestration tools offer security teams an integrated collection of processes and tools working in concert to automate otherwise tedious and time-consuming security management tasks.
Security orchestration relies on standards-based software and open application programming interfaces (APIs) to enable broad, easy interconnectivity between security systems. Taking advantage of the flexibility of open standards and RESTful APIs, the security team can simply and quickly connect SIEM, IDS, endpoint, threat intelligence and other security tools with the automation and orchestration capabilities.
An automated incident response and security orchestration solution enables the security team to model its alert response processes and automate them. It can triage and enrich alarms, open and close tickets, update rule sets, send emails to key stakeholders, and so forth, drastically cutting down on the time-consuming manual process of responding to threats. The team can assess 100 percent of threats as they arise. In contrast, a Ponemon Institute study found that most teams are limited to examining less than 30 percent of threats and triaging the rest. This approach can easily let a threat pass by that later turns into a costly incident.
Automated incident response with Swimlane
Swimlane offers an automated incident response and a security automation, orchestration and response solution that centralizes security operations activities. Swimlane manages and automates the response to security alerts and incidents identified by existing monitoring and detection systems. Swimlane also replaces slow, manual threat response capabilities with machine-speed decision making and remediation.
Swimlane tracks all enterprise security tasks, providing centralized access to cases, reports, dashboards and metrics for individuals and teams. It standardizes response and notification processes to mitigate risk, speed resolution and streamline communications. Its automation leverages vendor APIs and Software Defined Security (SDSec) methods to rapidly respond and prevent attacks earlier in the kill chain.
Working with Swimlane, the security team can speed up its pace of threat response and increase the percentage of threats it examines. Both of these improvements in security threat handling cut down on the risk of a costly delayed response.
To arrange for a demo of the Swimlane solution or to speak with one of our security architects to see if security automation and orchestration would be helpful to your organization, please contact us at 1.844.SWIMLANE.

